Empowering Cloud Security and Resiliency: A Guide to Read-Only Console Access
@glnds
In today’s digital landscape, cloud computing has become the backbone of modern business operations. However, as organizations increasingly rely on cloud services, security and data protection concerns have taken center stage. An approach that can help maintain a secure cloud environment is limiting console access to be read-only. Enforcing read-only access to the cloud console can help mitigate configuration drift, improve resilience, and protect against an account takeover.
In this blog post, we delve into the critical reasons behind implementing read-only access, its benefits, and practical steps to achieve this crucial security measure. Whether you’re a seasoned cloud administrator or just embarking on your cloud journey, join us as we explore how to bolster your cloud management strategy with enhanced security and control
Why should you go for Read-Only Access?
Enhance Reliability: Read-Only Access Encourages Infrastructure as Code
In the dynamic landscape of cloud computing, safeguarding the security and robustness of your digital infrastructure is paramount. A key strategy in fortifying resilience is the adoption of Infrastructure as Code (IaC), an approach that stands as the ultimate assurance for swift recovery. IaC’s ability to precisely replicate environments ensures rapid and error-free reconstruction, minimizing downtime and enabling rigorous testing and adaptable scalability.
By implementing read-only access to the web console, we reinforce the commitment to Infrastructure as Code, ensuring that all infrastructure modifications are meticulously tracked and controlled programmatically.
Enhance Security: From Generic Roles to Tailored Policies
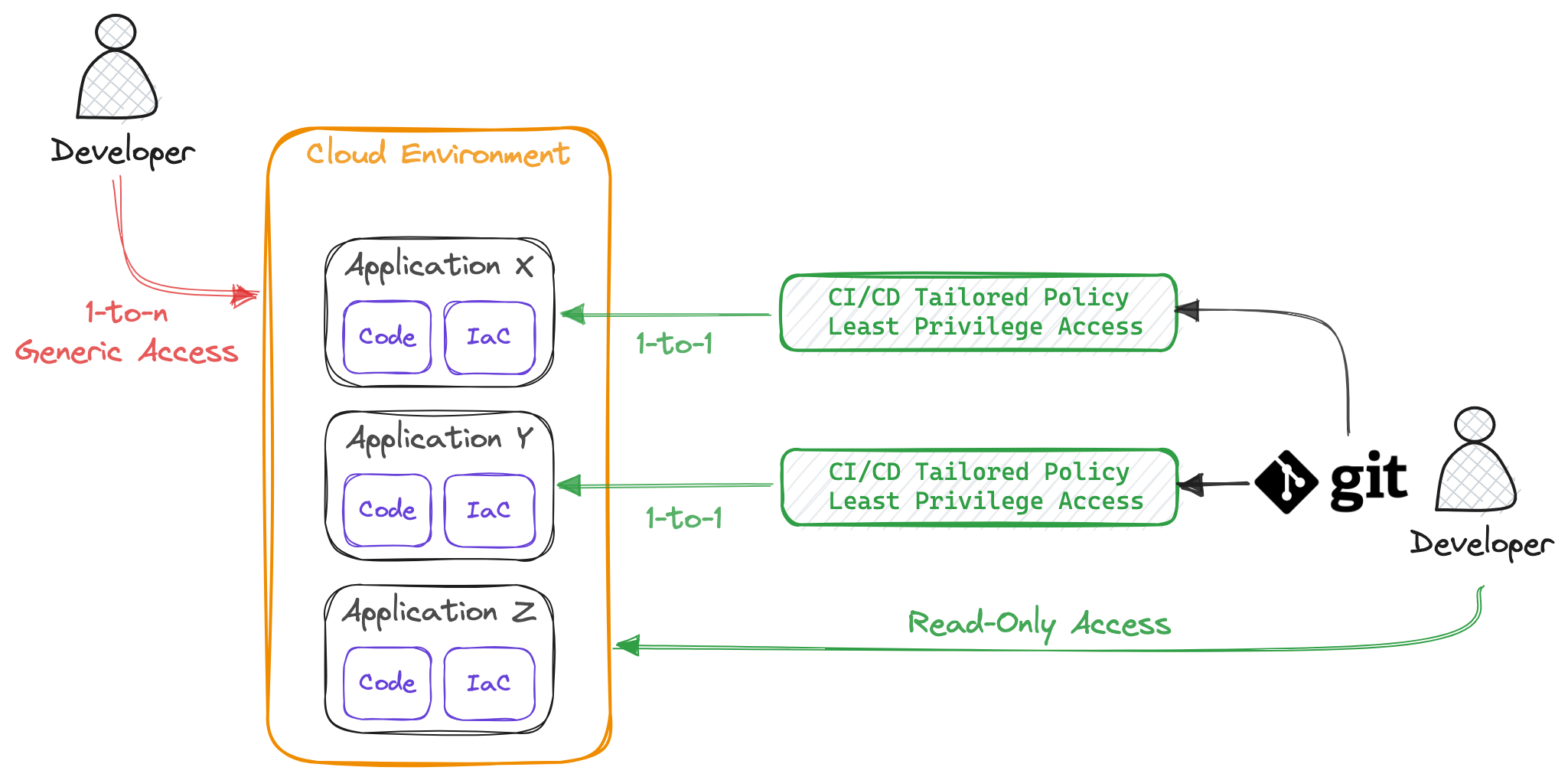
When it comes to security, simply granting read-only access doesn’t make things more secure. To truly enhance your security posture, it’s essential to examine how Identity and Access Management (IAM) users interact with your resources. Typically, IAM roles assigned to users tend to be quite generic. This generality often stems from the practice of hosting multiple services and applications within a single account. In such scenarios, a one-to-many relationship, where a user is associated with multiple applications, necessitates these generic user roles. However, if you aim to eliminate these generic roles and bolster your security, you should strive for a one-to-one relationship between a developer and the application.
One effective strategy for achieving this shift is to transition user access to CI/CD pipelines while routing interactions through Git. This approach allows to effectively limit the command line and console access to read-only privileges. It’s crucial to emphasize that in this setup, a well-defined pipeline policy that adheres to the principle of least privilege is a must. Deviating from the principle of least privilege and making the pipeline policy too permissive would only shift the potential security risks from the Web Console & CLI to Git.
By abandoning the one-to-many access policy for users and replacing it with a one-to-one pipeline-to-service policy, you can replace the generic user policy with a collection of least-privilege policies, each linked to a specific application’s pipeline.
The Complexities of Read-Only Access
While read-only access seems straightforward, it introduces a layer of complexity to your infrastructure management strategy and the shift to a read-only mode can present its fair share of obstacles. Nevertheless, you can enhance the process by initially establishing an interim role with limited privileges, thus ensuring that developers’ daily operations continue without disruption. This interim measure lays the foundation for a more sophisticated approach to authorization in the future. The ultimate goal is to implement only a read-only role along with a “break glass” procedure, reserved for highly exceptional circumstances.
Maintaining Swiftness and Preserving Velocity with the Interim Role
The primary objective for the interim role is to grant the absolute essential access without hindering a person doing his daily tasks. A new challenge that araises, once a door to an interim role is opened for requests seeking higher privileges, an influx of requests will begin pouring in. To mitigate the risk of an overwhelming number of requests and the proliferation of elevated privileges, it’s prudent to establish clear boundaries for what the interim role can and cannot encompass. This clarity not only streamlines the process but also ensures maintaining a careful balance between necessary access and preserving the integrity of our read-only framework.
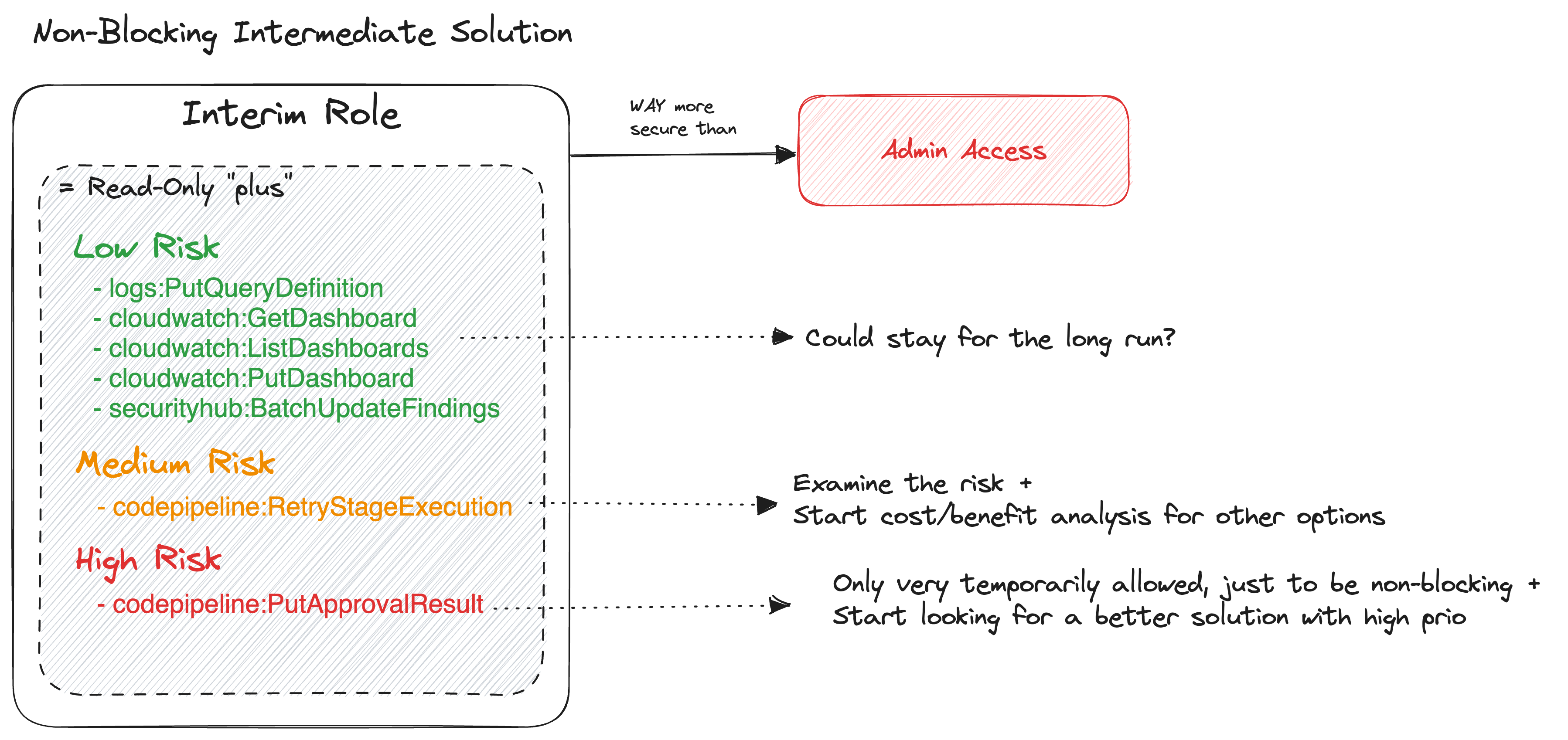
Therefore, the interim role does not exist to support ClickOps, as our ultimate goal is to manage all infrastructure through IaC. While certain scenarios may necessitate ClickOps temporarily, we view these as exceptions rather than the rule. With this vision in mind, we are contemplating the expansion of interim access, but strictly for non-security-critical tasks. This entails granting read access to Cloudwatch dashboards and enabling pipeline retriggering, while preserving stringent controls on actions like S3 bucket deletion. The interim access role is meticulously crafted to support a workflow where IaC takes center stage, effectively curbing ClickOps interventions. Simultaneously, it serves as a safeguard against frequent ‘glass-breaking’ incidents that may arise from tasks beyond IaC’s scope, provided they do not compromise security.
In essence, the interim access role serves a dual mission: it acts as a catalyst for widespread IaC adoption while upholding security standards, all without obstructing operational efficiency. This pivotal role represents a crucial link in the journey toward a more secure and resilient cloud infrastructure.

Transforming Security: Unveiling the Power of Break Glass Procedures and IaC
In our pursuit of operational excellence and enhanced security, we’ve set our sights on the North Star—streamlining our approach by relinquishing interim roles, embracing read-only access, and harnessing the power of Infrastructure as Code (IaC). Our mission is further fortified by the implementation of a “break glass” procedure, a safeguard designed for rare and urgent cases.
Before we delve deeper into this “break glass” solution, it’s essential to stress that this procedure is not to be employed for routine tasks. Instead, it stands as a safeguard for emergencies, necessitating vigilance and monitoring to maintain the highest levels of security. Amazon Web Services (AWS) has identified several scenarios warranting the activation of this emergency access, including the failure of an organization’s Identity Provider (IdP), security incidents involving IdP(s), issues with IAM Identity Center, or catastrophic events affecting an organization’s cloud or IdP teams. To ensure the integrity of this access, robust monitoring, alarms, and alerts should be in place, instantly signaling any usage.
As we rethink the concept of “break glass” access, we recognize that with IaC and Continuous Integration/Continuous Deployment (CI/CD) pipelines firmly established, the urgency to resort to emergency procedures should decrease. Aligning your CI/CD pipelines with your Recovery Time Objective (RTO) is a must to facilitate a controlled and efficient response to issues. The adoption of blue-green deployments and feature toggles becomes pivotal in this transformation.
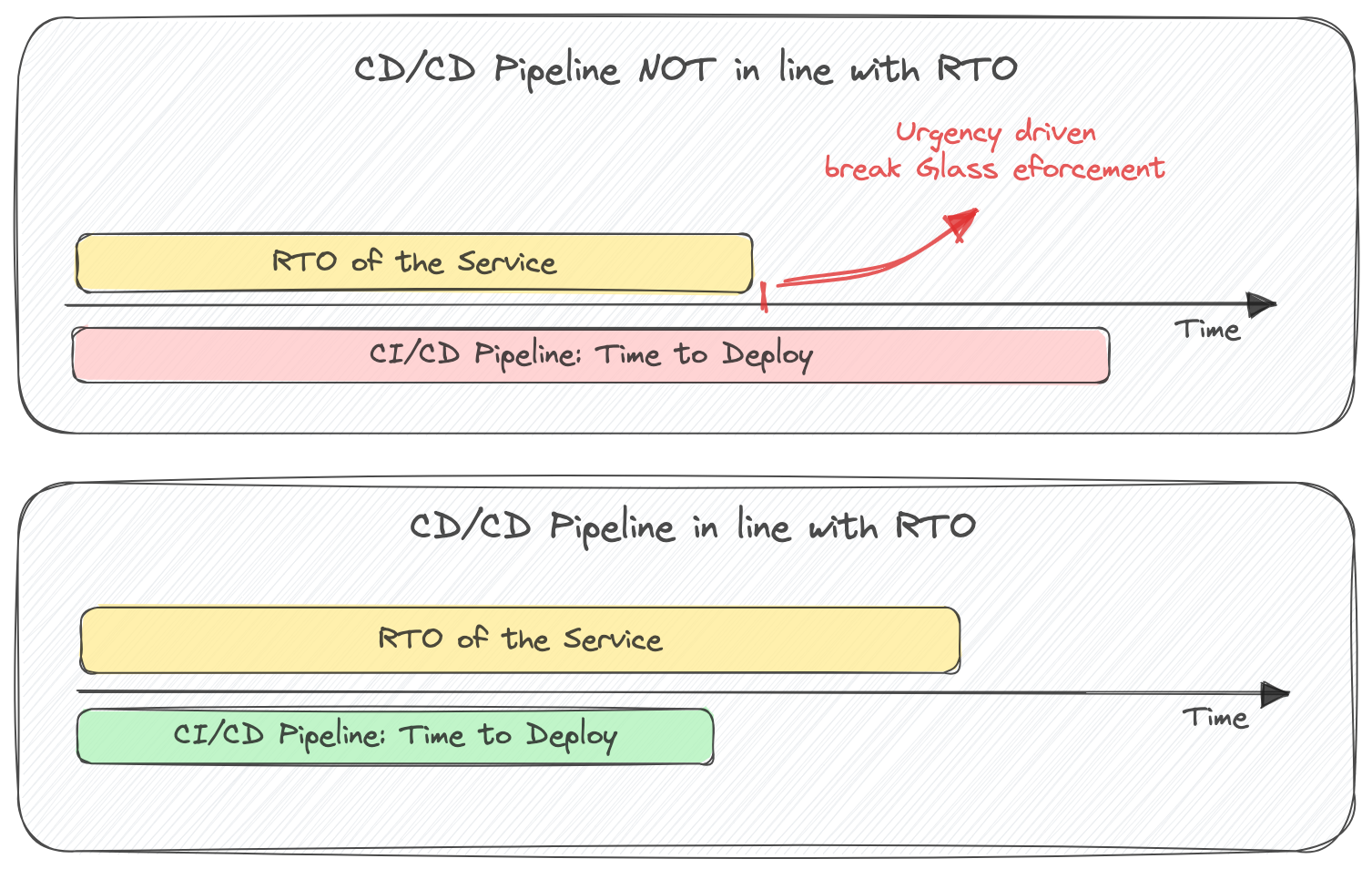
Blue-green deployments maintain two identical environments, allowing for seamless transitions between live and staging versions. Meanwhile, feature toggles empower you to activate or deactivate specific features without the need for redeployment. These strategies form a robust safety net, enabling swift issue resolution and rigorous testing, all while minimizing downtime.
Note: With Temporary elevated access management (TEAM) AWS has build its own open source solution that integrates with AWS IAM Identity Center and allows you to manage and monitor time-bound elevated access to your multi-account AWS environment at scale.
Conclusion
Our journey to fortify cloud security and resilience through read-only console access and Infrastructure as Code (IaC) has unveiled a powerful strategy for safeguarding your digital infrastructure. By embracing read-only access and refining our identity and access management policies, we can enhance reliability and security in a cloud-centric world. However, it’s crucial to acknowledge that the transition to read-only access introduces complexities, which we address through the strategic use of interim roles and a well-defined “break glass” procedure for exceptional situations.
In the realm of cloud security, the future holds great promise. By embracing these strategies and staying committed to the principles of security, resilience, and innovation, we pave the way for a brighter and more secure digital landscape. Thank you for joining us on this journey towards a more secure and efficient cloud management strategy.